In this post I’m going to allow EC2 to use S3 to store files. I’m going todo this 2 ways:
- First simple access (less secure, not for production), EC2 instance can do anything on S3
- Secondly , I will limit what the EC2 instance can do (read, write only on a specific bucket using its ARN )
Simple Access for EC2 to use S3
The Process
- Create Policy to allow access to service (S3 everything)
- Create Role (and attach policy from step 1)
- Give the EC2 instance the Role
- Verify it works using AWS CLI (from EC2 server), to upload a file
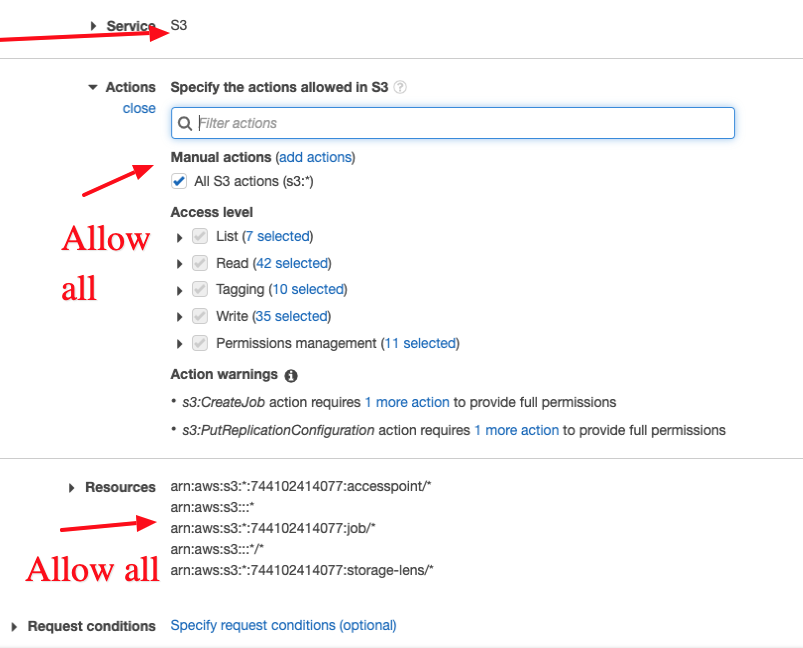
1 Create Policy to allow access to service (S3 everything)
- Go to IAM Dashboard, then Create Policy from left menu.
- Select the service to allow access to (S3 in this case)
- Allow all Actions
- Allow all Resources
- Goto step step (Review policy)
- Enter name and Create Policy (I called mine: GreenBoxAllAccessToMyS3)
2 Create Role (and attach policy from step 1)
- Back to IAM Dashboard, select create Role from left side
- Select the EC2 service (you want to allow this), and move to next step
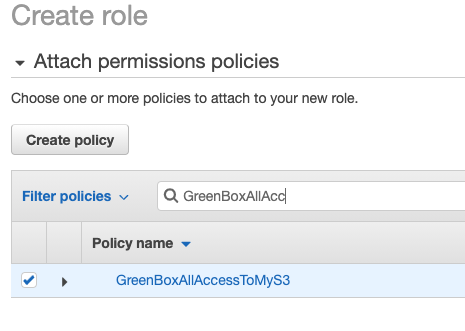
- Search for the Policy you created and check it (see screenshot below), move to next
- Give the role a name and Save/Create ( I called it GreenBoxRoleAllowAllAccessToS3FromEC2 )
3 Give the EC2 instance the Role
- Go to the EC2 instance, and attach the Role just created
- Checkbox instance -> Actions -> Security -> Modify IAM role
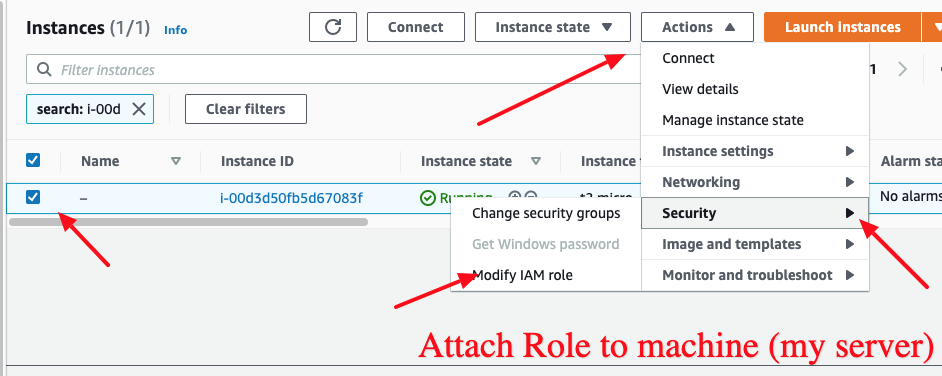
- Find the Role just created and Attach it
4 Verify it works using AWS CLI (from EC2 server), to upload a file
- Finally SSH onto the server (you can use Connect in above image)
- Create a file and upload it to S3 using command below:
aws s3 cp test.txt s3://for-testing-access/test2.txt
for-testing-access is my bucket.
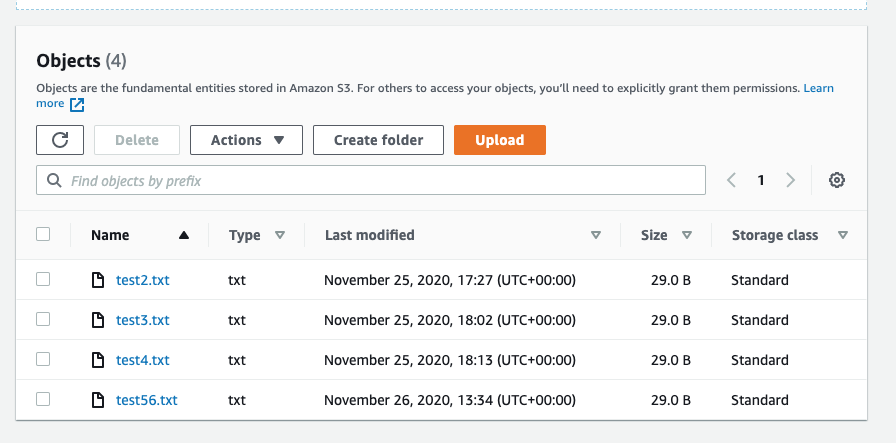
Finally check in the bucket to make sure the file is there:
Version 2 – Access for EC2 to use S3 (limited permissions and specific bucket)
I’ll now detail how to tie this down abit, so that the EC2 instance with the Role can only do limited things (restricted permissions), to a specific Bucket (based on the ARN of that Bucket).
- First copy the ARN of the S3 bucket to the clipboard (S3 dashboard)
- Go back to our policy on IAM Dashboard ( I called mine: GreenBoxAllAccessToMyS3 ).
- Search for it and then click it
- Click ‘Edit Policy’
- Under Actions section we’re going to edit so it just allows Read/Write access to a specific Bucket (it would be useful to allow List also, but I won’t for brevity here).
Check all the permissions (actions) that have Object in their names for Read and repeat for the Write section (so you can add Objects or read Objects from the bucket, you could limit it further but for speed click everything for Object).
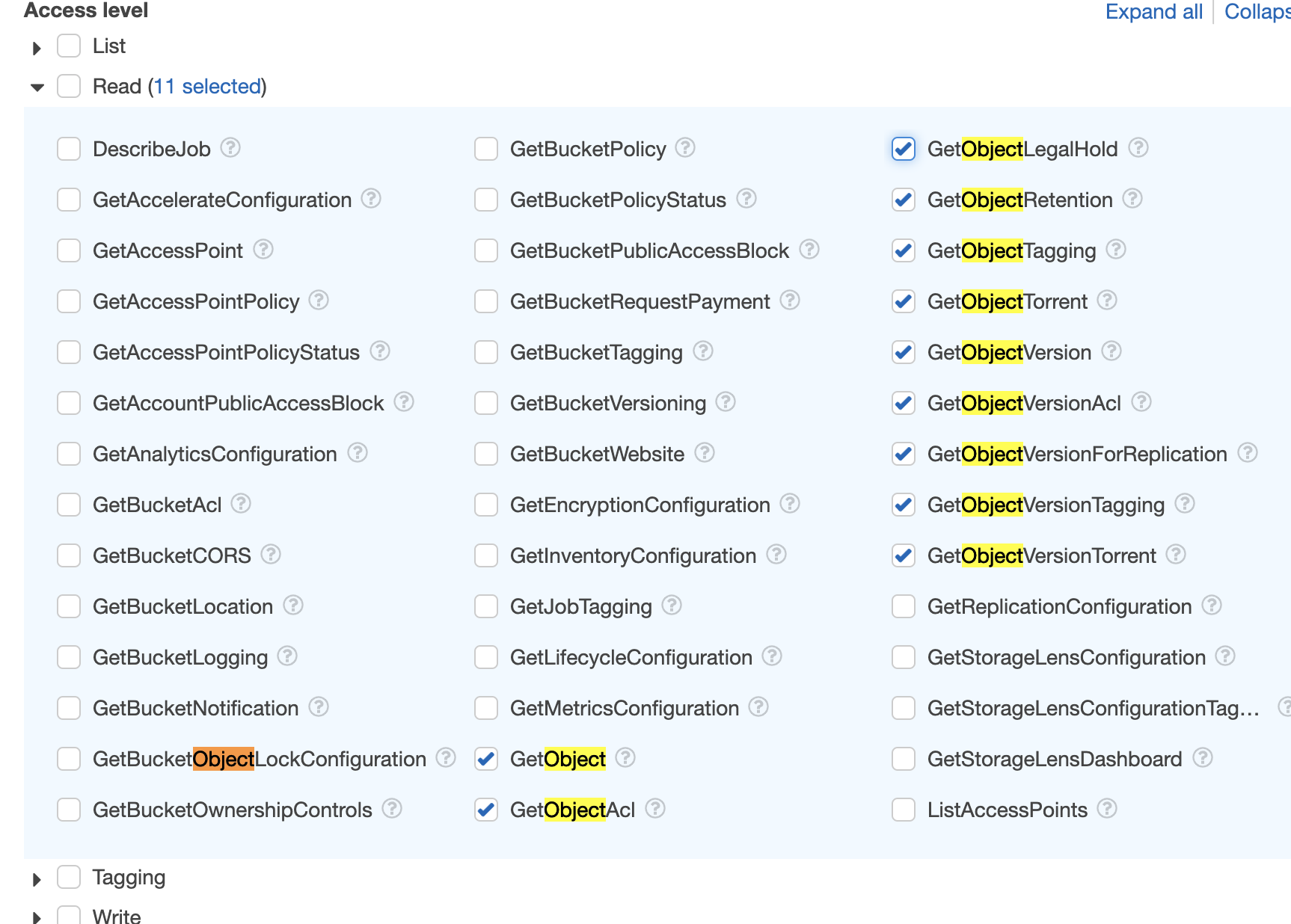
Remove any actions / permissions so you only have to add an ARN for the objects (which are linked to a Bucket), ie the Resources section should be like below (and we’ll add the bucket ARN in):
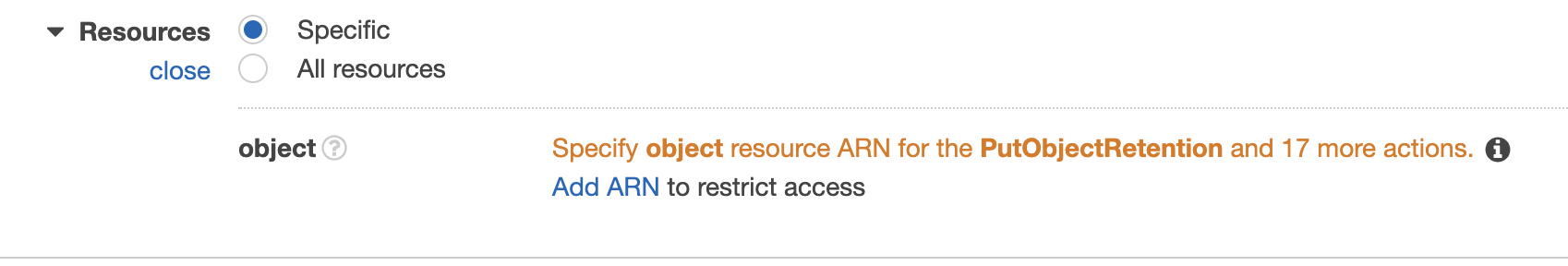
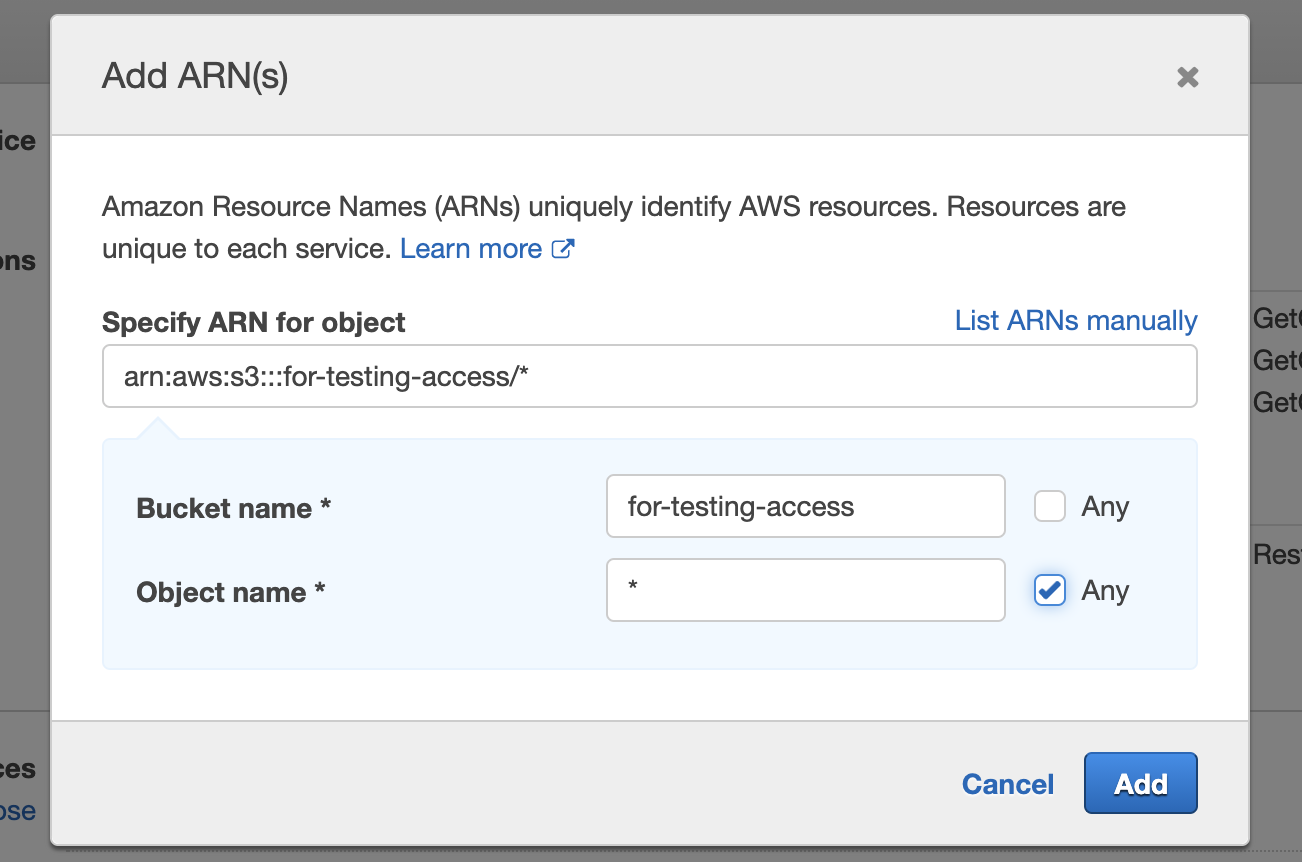
We can then add the ARN of the specific bucket as above, and star for object (ie allow access to all Objects in Bucket).
Add , then select next / Review to go through the steps to save the policy.
Finally test as we did before (use SSH to test can we), add a file to the bucket ( then check in the bucket via the AWS S3 UI/Dashboard to see if its there).
References
https://aws.amazon.com/premiumsupport/knowledge-center/ec2-instance-access-s3-bucket/